The Compliance Challenge
Organizations face increasing pressure to demonstrate comprehensive infrastructure governance while managing escalating compliance requirements. Auditors demand detailed evidence of technical vulnerability management, but most teams struggle to bridge the gap between technical infrastructure data and communicating business risk.
Key Challenges:
- Fragmented Risk View: Security and lifecycle risks are managed in separate silos.
- Compliance Preparation Overhead: Weeks spent gathering evidence for auditors and executives.
- Framework Complexity: Meeting multiple requirements (ISO 27001, NIST, CISA) with limited resources.
- Executive Communication: Translating technical infrastructure risks into business language.
- Continuous Monitoring: Maintaining compliance posture between formal assessments.



Our Proactive Intelligence
Our risk and compliance assessment further expands on the lifecycle intelligence model by incorporating data from critical external sources of truth, such as the Common Vulnerabilities and Exposures (CVE) and Known Exploitable Vulnerabilities (KEV).
By combining external threat data with your infrastructure lifecycle intelligence, we provide precise visibility into which vulnerabilities in your environment pose immediate risks and require urgent attention.
- Infrastructure Mapping: Direct correlation between external threats and your specific devices.
- Lifecycle-Aware Vulnerability Management: Identify vulnerabilities in unsupported software.
- Risk Prioritization: Focus on exploitable vulnerabilities with active threats.
- Comprehensive Coverage: Beyond endpoints to include network infrastructure, security appliances, and IoT devices.
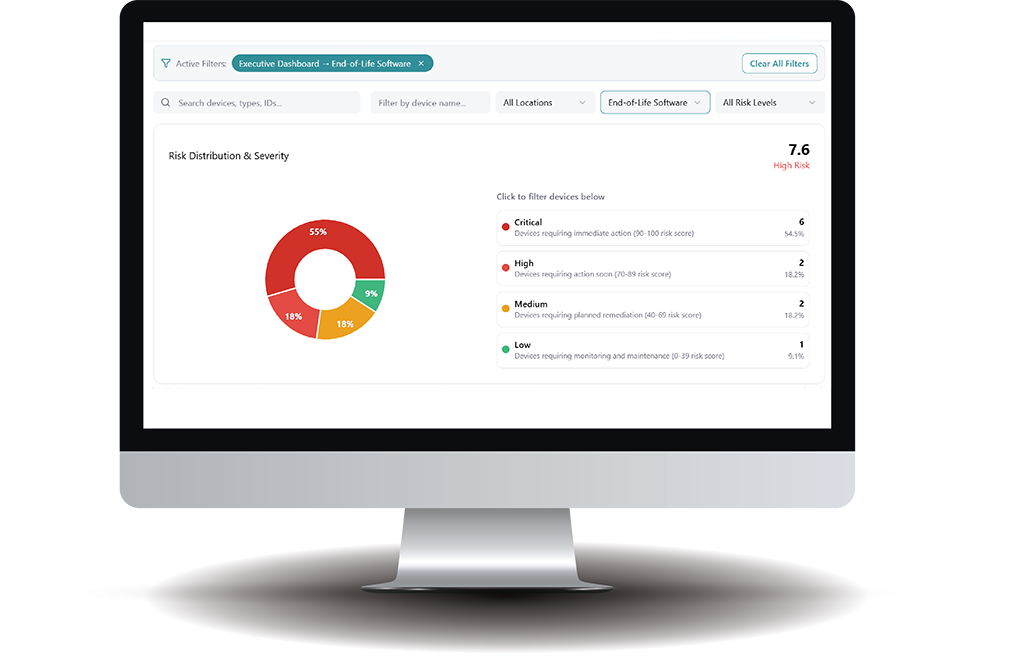
Key Benefits
- Proactive Risk Management: Identify risks before they become incidents.
- Complete Vulnerability Visibility: Beyond traditional scanning to include lifecycle risks.
- ISO 27001 Readiness: Automated assessment against Clause A.12.6.1 and A.8.1 requirements.
- Framework Alignment: Evidence for NIST Cybersecurity Framework and CISA Controls implementation.
- Executive Communication: Clear business risk language for leadership presentations.
- Audit-Ready Documentation: Executive summaries, technical reports, and evidence packages.
See immediate improvements in compliance and risk understanding.
Faster compliance assessments with automated framework alignment.
Reduced audit preparation time through ready-to-present documentation.
Enhanced risk prioritization combining lifecycle and external threat data.
Improved executive reporting with business-focused risk communication.