Information Exists, But It's Unusable
The information is out there: vendor updates, end-of-life notices, critical vulnerabilities, but it’s buried in portals, PDFs, and product release notes. IT teams waste countless hours manually tracking versions, EOL status, and support timelines across multiple vendor portals and spreadsheets.
Manual Tracking Challenges:
- Fragmented Data Sources: Vendor portals (Cisco, Fortinet, Palo Alto), Excel sheets, internal wikis.
- No Cross-Vendor View: Siloed insights that don’t provide comprehensive risk assessment.
- Manual Effort: DIY lifecycle tracking that’s not scalable or auditable.
- Missing Risk Model: No way to prioritize what matters most to your business.
We Complete What's Missing in Your Existing Tools
Cadents pulls vendor data together and makes it usable by mapping it to your actual infrastructure. Our platform augments your existing tools by layering in lifecycle intelligence that they lack.
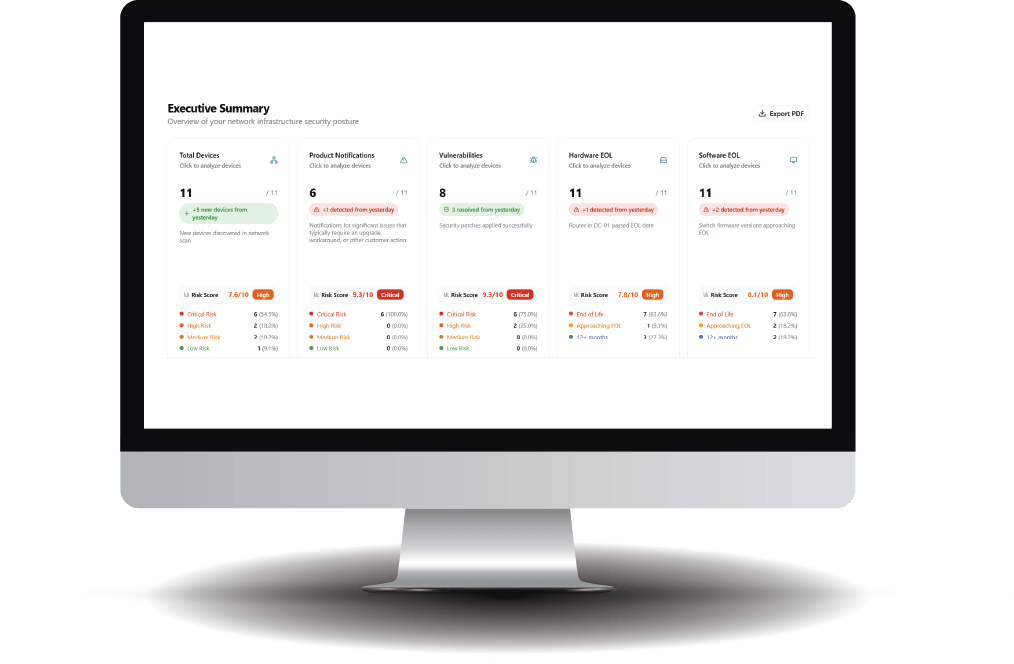
Our AI-driven lifecycle intelligence platform compares your network infrastructure software against the vendor’s recommendations. It’s simple, easy to use, and provides information at your fingertips, allowing you to make informed decisions within minutes rather than hours or days.
Drill-down capabilities enable you to delve deeper into each area, viewing associated assets and receiving recommendations for remediation to mitigate risk and safeguard your company’s most critical assets.
- Real-Time Lifecycle View: Live visibility into what’s outdated, unsupported, and exposed across all vendors.
- Cross-Vendor Intelligence: Unified view across vendors.
- Risk Prioritization: Intelligent scoring that focuses your team on what matters most.
- Actionable Data: Convert complex vendor bulletins into structured, actionable insights.
Key Benefits
- Eliminate Manual Tracking: Stop chasing vendor portals and maintaining spreadsheets.
- Complete Infrastructure View: See lifecycle status across all vendors in one place.
- Focus on What Matters: Risk-based prioritization guides resource allocation.
- Integrate Seamlessly: Works with your existing CMDB, ITSM, and security tools.
- Stay Compliant: Built-in alignment with major security frameworks.
See improvements in risk visibility and infrastructure efficiency.
Reduced infrastructure research time with real-time vendor intelligence.
Faster risk identification across multi-vendor environments.
Improved compliance readiness through framework-aligned reporting.
Enhanced decision-making speed with actionable lifecycle data.